🔪 TL;DR:
- What’s PIM? Not a crypto scam. It’s how you stop Dave from 1st level Support from being Global Admin at 3AM.
- Why care? Because attackers love admin rights more than interns love leftover cake.
- Strategy? Least privilege, approvals, and never trusting anything “temporary.”
- Bonus? I’ll show you how a real-world PIM rollout looks.

🧂 What the Hell is PIM Anyway?
Privileged Identity Management (PIM) is Microsoft’s way of helping you stop handing out permanent superpowers to everyone who asks nicely.
Think of it like a bouncer at your admin club: you only get in if you have a reason, a time limit, and your name's on the list.
PIM sits inside Entra ID (fka Azure AD — yes, another rebrand because Microsoft loves confusion) and helps you:
- Grant time-limited admin access ⏱️
- Require approvals before roles are activated ✅
- Ask for justifications 📝
- Keep receipts for every click 💰
The point? Reduce the window of opportunity for attackers. If no one has standing admin access, there's nothing juicy to hijack at 3 in the morning.
Honestly, it’s less about being paranoid and more about being realistic. The days of "just give them Global Admin" are long gone. Or at least, they should be.
🔍 Strategic Thoughts – Before You Just PIM It
You don’t just slap PIM on your tenant and walk away like a hero in an action movie. It needs thought. Planning. Diagrams. Probably snacks.
1. Know Your Roles (and Regrets)
Step one: figure out who has what. This part is always fun (read: horrifying). Export role assignments using PowerShell or the Entra portal. If you find interns with Exchange Admin, congratulations — you’re not alone.
2. Who Owns What? Seriously.
Every role should have an owner. That person isn’t just approving requests — they’re the human firewall. They need to:
- Understand why someone wants a role
- Monitor activity
- Deal with the fallout if something explodes
3. Build Role Tiers Like You Mean It
All admin roles aren’t created equal. Some can nuke your tenant. Others can just poke around a bit. You need clear PIM policies per tier:
- 🔓 Low-risk roles: auto-approve, maybe skip MFA
- 🔒 High-risk roles: require justification, approval, blood sample, and maybe a background check
🧾 Here’s a Cheat Sheet of Roles You Really Should Wrap in PIM:
| Role Name | Why It's Spicy |
|---|---|
| Global Admin | Can do literally anything, including nuking your org. |
| Privileged Role Admin | Can hand out roles like candy. Scary. |
| User Admin | Reset any password. Hello, account takeover. |
| Exchange Admin | Email snooping? Check. Auto-forwarding? Yup. |
| SharePoint Admin | All your company files, one click away. |
| Security Admin | Disable security alerts. Like turning off your smoke alarm during a fire. |
| Conditional Access Admin | Bypass MFA. Just what attackers love. |
| App Admin | Approve shady OAuth apps. Shadow IT's best friend. |
| Billing Admin | Buy stuff. With your budget. |
| Auth Policy Admin | Create backdoors. With a smile. |
| Teams Admin | Chaos in meetings? Yep. |
If even one of these is permanent, you're basically leaving the vault door open and going on vacation.
Global Admin should always be assigned to only one User:
Your Break Glass Admin which is never going to be used, unless your Company is attacked by Korean Hacker Squad at 8am. Global Admin should always be secured with a Phishing Resistant MFA Method - in the best Case with Fido Keys.
🔐 Least Privilege: The Only Religion That Matters
Let’s say it again for the people in the back:
No. More. Standing. Admin. Access.
PIM enforces just-in-time access, meaning:
- No one has constant elevated privileges
- Access is only granted when needed — and only for long enough to get the job done
- Every action is logged and reviewable
The less time someone spends in a powerful role, the less time an attacker has to exploit it. Simple math. And when your compliance folks ask for an audit trail, you’ve got it. All of it.
Also, if someone does try something shady, you get alerts — in real-time. With the right automation (hello Graph API and Sentinel), you can even auto-disable accounts or notify your SOC while you're still sipping coffee.
🛠️ Cloudcook's Guide to Rolling Out PIM Like a Pro
Let’s talk implementation — no theory, just practical, tested chaos.
🧑🍳 Step 1: Find the Mess
Run access reviews and prepare to be shocked. If it turns out four interns have SharePoint Admin and one dude has Global Admin "just in case" — you're not alone.
🗃️ Step 2: Rip Off the Band-Aid
- Revoke unnecessary access
- Get rid of legacy roles
- Align to Microsoft’s built-in role model (and try not to scream)
📋 Step 3: Set Up Real-World Policies
| Role | Activation Time | MFA | Approval | Justification |
|---|---|---|---|---|
| Global Admin | 1h | ✅ | ✅ | Required |
| Teams Admin | 4h | ✅ | ❌ | Optional |
| Security Reader | 8h | ❌ | ❌ | Optional |
🔄 Step 4: Set Up Monitoring and Alerts
Every role activation should be logged and ideally piped into your SIEM. If someone triggers Global Admin at 01:27 AM — you want to know. Immediately.
Better yet, set up automated workflows using Power Automate or Sentinel to:
- Flag unusual access patterns
- Notify managers or the SOC
- Automatically revoke access after X hours
🧼 Step 5: Schedule Reviews (and Actually Do Them)
Automate monthly reviews. If someone ignores the email reminders? Remove access. No mercy.
Auditors love this stuff. And it makes it way easier to prove you're not handing out keys like party favors.
💡 What Could Possibly Go Wrong? (Oh, So Much)
- People will complain. “I need Global Admin to fix a Teams channel” — no you don’t, Steven.
- Too many prompts = fatigue. Don’t go overboard or people will just click yes to everything.
- Licensing shock. PIM needs Entra ID P2. If you're on Basic, you're outta luck.
- No plan = chaos. Without clear owners and policies, your PIM rollout will be more mess than magic.
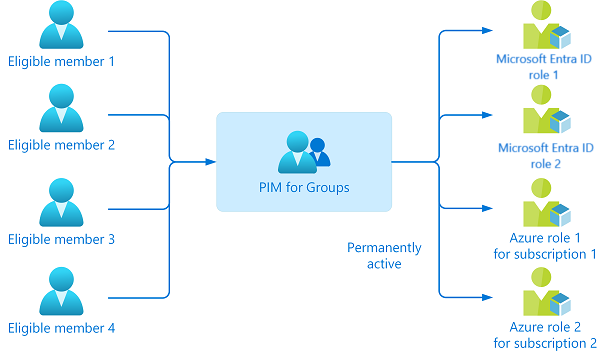
👥 Bonus: PIM for Groups — Because Groups Deserve Love Too
You thought PIM was only for role assignments? Oh no, my friend — it also works with groups. Because what’s better than managing one privileged user? Managing twenty of them with one misconfigured group.
Here’s the deal: some access in your org isn’t granted directly via roles, but through group membership. Maybe you’ve got a group like Privileged Exchange Admins that grants mailbox access, or Defender Masters 3000 that unlocks your security center. Instead of letting people sit in those groups forever, you can PIM the group membership.
🔄 How PIM for Groups Works:
- You assign eligible users to a group
- They must activate their membership (just like a role) when they need it
- You can require justification, approval, and set time limits
- Their membership is automatically revoked after the activation period ends
Basically, you’re wrapping a layer of control around dynamic access — and that means fewer standing privileges and tighter blast radius if something goes sideways.
💡 Use Case: Got an on-call security team? Let them PIM into a group that grants full access to Microsoft Defender or Sentinel — but only while they’re on shift. At all other times? Read-only or nothing at all.
PIM for groups is a game-changer if you're using role-based access control (RBAC) through Entra security groups, or if you've got old habits of assigning app permissions via Azure AD groups.
🧩 Bonus: Using Authentication Context with Conditional Access + PIM
Okay, now we’re entering galaxy brain territory — combining PIM with Conditional Access and authentication context. Why? Because just activating a role shouldn’t mean you can access everything, everywhere, all at once.
Here’s the vibe: even when someone elevates to a privileged role using PIM, you can still slap some extra rules on what they can do — based on where they are, what they’re accessing, and how they’re logged in.
🔐 How It Works:
- Define an authentication context in Entra ID. Think of it as a label: “Only let users through if they’re wearing MFA armor and standing on a trusted device.”
- Create a Conditional Access policy targeting that authentication context.
- Apply that context to apps or resources, like the Azure Portal or Defender.
Now here’s the kicker: In your PIM settings, require that this authentication context is satisfied before a user can activate the role.
💥 Result? You’ve got:
- Time-based access ✅
- Just-in-time elevation ✅
- Conditional Access validation on top ✅
It’s like PIM, but with a bouncer that checks your ID and makes you solve a riddle to get in.
This is especially spicy for high-value roles like Global Admin or Security Admin. No trusted device? No elevation for you. Sitting on a sketchy WiFi in a hotel? Not today, buddy.
☕ Final Thoughts from Cloudcook
PIM isn’t just a checkbox. It’s your frontline defense against accidental chaos and targeted attacks.
When you implement it right:
- 🚫 Overprivileged chaos turns into organized control
- 🔐 Roles become manageable, auditable, and locked down
- ⏰ Access is granted only when needed, never longer
- 😎 You sleep better at night
So go ahead, enable PIM, roll out those policies, and enjoy watching your risk graph shrink.
Remember:
Least privilege isn’t about being paranoid — it’s about being prepared.



