Let’s face it: if your security plan still includes the phrase "we trust our users," you’re basically handing out admin rights at a toddler’s birthday party. It’s 2025. My Grandma’s phishing filter is sharper than half the SIEM configs out there. That’s why today, we’re shifting into full tinfoil-hat mode: Zero Trust.
But instead of buying a 400-page Gartner report, or hiring a consultant who quotes Sun Tzu while charging 400 Money per hour to say "it depends," we’re going full tilt with CloudCook’s Zero Trust Survival Kit — powered by Intune and Entra ID. No fluff. No BS. Just hardened endpoints, conditional access, and enough memes to soothe the soul.
Sun Tzu’s Guide to Zero Trust 🥷
Sun Tzu and Zero Trust are spiritual siblings — both are all about constant verification, strategic paranoia, and knowing your stuff better than your CISO knows your budget.
So, let’s stir-fry some ancient wisdom into our modern dumpster fire security landscape:
🥷 “Know your enemy and know yourself — and you need not fear the result of a hundred battles.”
That’s Zero Trust 101. Don’t trust users. Don’t trust devices. Heck, don’t even trust your printer — it’s probably phoning home to some sketchy cloud.
Validate everything, log it, and double-check it. If you’re not authenticating every access request like it’s a secret vault, you’re doing it wrong.
🥷 “The supreme art of war is to subdue the enemy without fighting.”
In Zero Trust, that means don’t wait for the malware to knock on your firewall — block that shady IP range from Albania before it starts probing your Remote Desktop Gateway.
Good Zero Trust strategy neutralizes threats pre-breach, so your SOC isn’t running around like headless chickens after someone clicked “Free iPad.”
🥷 “If you know the enemy and know yourself, you need not fear the outcome of a hundred battles.”
Yup, still relevant. In Zero Trust, it means understand user behavior, device posture, app context, and don’t forget the sneaky stuff — like that idle service account doing privilege escalation in the background.
Visibility is power. Blind trust is a compliance nightmare waiting to happen.
🥷 “All warfare is based on deception.”
Translation: your attacker is already faking being legit.
So why would you skip behavioral analytics, conditional access, or MFA?
Assume compromise. Then assume they’re trying to fake being Fritz from Accounting.
Then block Fritz from accessing SharePoint from a Chromebook in Belarus.
🥷 “Strategy is like water — it adapts to its environment.”
Zero Trust isn’t a one-time config change in Intune, Sabine.
It’s a living, breathing paranoia engine that flows around new risks.
You patch, update, tweak policies, log everything, and treat every connection like it might try to steal your lunch money.
So yeah — Sun Tzu wasn’t just a war nerd.
He was the original Zero Trust architect, minus the Azure license.
🚫 What Is Zero Trust (Without the Marketing BS)?
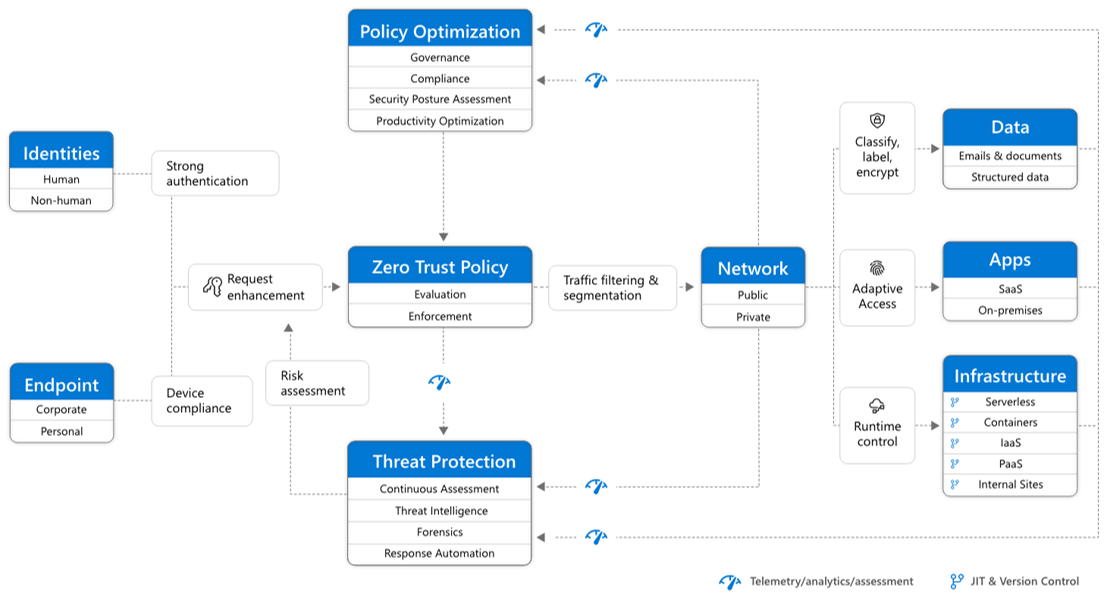
Zero Trust means: Assume breach. Verify explicitly. Use least privilege. 🧠🔐
Translation for sysadmins: every user, device, app, and rogue smart toaster needs to prove it belongs — every single time. Even Fritz from accounting. 🦆
According to Microsoft's holy scrolls, Zero Trust is based on six holy pillars:
- 👤 Identity
- 💻 Devices
- 📱 Apps
- 📂 Data
- 🏗️ Infrastructure
- 🌐 Networks
Microsoft also reminds us: Zero Trust isn’t a product — it’s a security strategy. Cool. But can it deploy apps on time?
🛡️ Pillars of Zero Trust You Can Actually Deploy (Without Crying)
- Strong Identity = Verified Identity 🪪
- 🔐 Use Entra ID to enforce MFA like it’s a religion. No MFA? No login. No mercy.
- 🌍 Roll out risk-based Conditional Access. Logging in from “Accidentally Clicked a Link”? Challenge accepted. Or denied.
- ⛔ Nuke legacy authentication. Like, yesterday. It’s older than your backup tapes.
- 🕵️♂️ Identity protection that calls out weird logins faster than your aunt replies to a WhatsApp scam.
- Devices You Can Trust 🖥️
- 🧼 Deploy Intune like Oprah: “You get enrolled! And you! And you!”
- 🛡️ Mandate compliance settings that even cyber gremlins fear: BitLocker, Secure Boot, real AV (not your cousin’s cracked copy).
- 🚷 Use Compliance + CA to block devices you wouldn’t let near your Wi-Fi.
- 🧠 Let Defender for Endpoint score your devices. If it scores like your high school math test — deny it.
- Least Privilege Access 🪄
- 🧙♂️ Enable PIM. No one needs 24/7 Global Admin. Not even you, Florian.
- 🪪 Build custom roles like a paranoid Lego master. Avoid Role Roulette unless you're bored.
- 🔔 Alert like your back account balance depends on it. Because it does.
- Access Policies That Actually Do Stuff 🔐
- 🧩 With Conditional Access, enforce:
- 🔑 MFA (duh)
- ✅ Compliant devices only
- 🌍 Safe IPs and regions
- 🚫 Auto-nuke risky users (sorry, Florian)
- 👻 Always start with report-only mode. Unless your job title is “Chaos Engineer.”
- 🕶️ Use Defender for Cloud Apps to micromanage sessions like a security freak on espresso and a hardcore gym booster.
- 🧩 With Conditional Access, enforce:
- App Governance & Control 📱
- 🗂️ Publish apps with SSO. Fewer passwords = fewer Post-it note disasters.
- 👮 Control download behavior like an overprotective digital parent.
- 🚫 Lock down OAuth like your career depends on it. Because it might.
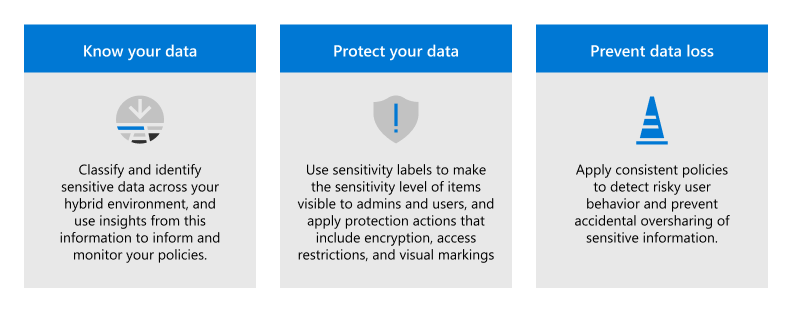
- Data Protection 📦
- 🏷️ Tag and label everything. Seriously. Treat data like it's radioactive.
- 🔐 Encrypt like you’re guarding grandma’s secret lasagna recipe.
- 📜 Audit logs? Yes. All of them. Even the ones you swear you’ll check later.
- Infrastructure & Network Fortification 🌐
- 🧱 Let Defender for Cloud judge your infrastructure like Dieter Bohlen on a bad day.
- ⏱️ Use JIT access like an insecure teenager: short bursts, constant supervision.

🚀 Getting Started: A Lazy Admin's Checklist (With Feeling)
- ✅ Baseline Conditional Access policies 🔒
Block legacy auth, enforce MFA, allow only compliant devices. Basic hygiene, people. - 💻 Enroll all devices in Intune 🧽
Even the haunted MacBook from accounting. - 🛡️ Set up compliance policies 🔐
Encrypt, secure boot, antivirus. If your SOC team isn’t grinning, try harder. - 👀 Deploy CA in report-only mode 📊
Watch the chaos before it goes live. Popcorn optional. - 🧙♂️ Enable PIM 🕵️
Because “Oops, I was logged in as Global Admin” isn’t an acceptable postmortem. - 🚫 OAuth consent restrictions 📵
That flashlight app again? Really? - 🧠 Integrate Defender for Endpoint ⚙️
Risk-based decisions that make sense. Finally. - 🧱 Enable Defender for Cloud 🧟
Not just a compliance tool — it’s a “don’t get fired” tool. - 🔏 Deploy DLP & labels 💌
Because data spillage is not a team-building activity. - 📋 Enable audits & alerts 👁️
Log it. Sift it. Meme it. - 🧹 Quarterly cleanup reviews 🔁
Roles, policies, devices. Delete like you mean it.
🧾 Prerequisites: What You’ll Need Before You Can Go Full Zero Trust 🚀
Let’s not kid ourselves — Microsoft loves licenses like Dogs love snacks . Here’s what you’ll need before you can start locking things down like a paranoid ninja:
- 💳 Microsoft 365 E5 or Microsoft 365 E3 + add-ons
- If you want all the toys (Defender, DLP, PIM, etc.), go for E5. E3 users: prepare to a-la-carte your way to bankruptcy.
- 🔐 Entra ID P2 (formerly Azure AD Premium P2)
- Needed for PIM, risk-based Conditional Access, Identity Protection, and advanced reporting.
- 🛡️ Microsoft Defender for Endpoint Plan 2
- Get those juicy risk signals and automated investigations. Also lets you slap down malware with a righteous fury.
- ☁️ Microsoft Defender for Cloud Apps
- If you want session control and shadow IT detection without a seance.
- 📂 Microsoft Purview Data Loss Prevention (DLP)
- Included in E5 or available standalone. Labels, policies, and the ability to catch Sabine emailing payroll again.
- 🧱 Microsoft Defender for Cloud
- For infrastructure security posture, Secure Score, and the occasional guilt trip.
- 🧙♂️ Licensing sanity and PowerShell skills
- Because the portal will fail you. Scripts will not
🚒 Wrap-Up: Zero Trust or Zero Sleep?
Zero Trust isn’t a button you click. It’s a way of life. Like quitting smoking — but with more PowerShell and less judgmental looks from strangers.
With Intune + Entra ID, you’re not just protecting endpoints. You’re protecting dignity, uptime, and probably your bonus.
And always remember: the only thing you should trust by default is that nothing will work the first time.


