Cybersecurity is all about to be secure. What does "secure" means exactly?
With "secure" we mean that we want to protect our computers, networks, devices, and data from digital attacks, unauthorized access, theft, or damage. The main goal is to confirm that confidentiality, availability, and integrity are are maintained.
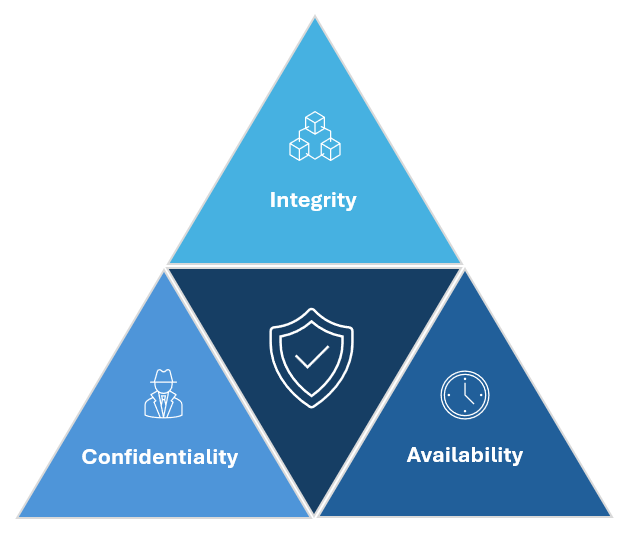
What is the cyber security CIA triad?
The cyber security triad refers to the model that incorporates the three main considerations for any cybersecurity work or designing a system/environment:
Confidentiality
This is the consideration that most people would be familiar with when they think “cybersecurity”: confidentiality is the process of protecting data and information from unauthorized access attempts i.e. only people who need to see information are able to access it. Not all data is created equal though, and data is usually categorized and protected based on how much damage would occur if it were accessed by the wrong people.
Integrity
Refers to protecting the accuracy and trustworthiness of data contained within environments and not allowing the data to be altered or amended by unauthorized individuals. e.g. a student amends their date of birth on their driver record at the DMV to make them older so they can get their license reprinted with an earlier date of birth to buy alcohol.
Availability
This is a consideration across operational IT, but availability is also important for cybersecurity. There are specific types of attacks that target availability that security professionals must protect against (e.g. distributed denial of service – DDoS – attacks).
Cybersecurity CIA Triad
What are authenticity, nonrepudiation and privacy in the context of cyber security?
These are additional important concepts that relate to ensuring the security and trustworthiness of systems and data:
Authenticity - refers to the assurance that the information, communication, or entity you are interacting with is genuine and has not been tampered with or altered by unauthorized parties.
Nonrepudiation - is the concept of ensuring that a party cannot deny their involvement or the authenticity of a transaction or communication. It prevents someone from claiming they didn't send a message or perform a particular action when there is evidence to the contrary.
Privacy - refers to the protection of sensitive and personally identifiable information from unauthorized access, use, disclosure, or manipulation. It involves controlling who has access to personal data and how that data is collected, stored, and shared.
What is a cybersecurity threat?
A cybersecurity threat refers to any potential danger or risk that has the potential to compromise the confidentiality, integrity, or availability of data or IT systems. These threats are posed by malicious actors who attempt to exploit vulnerabilities in order to gain unauthorized access, steal sensitive information, disrupt operations, or cause harm to individuals, organizations, or even entire nations. Cybersecurity threats can take various forms and target different aspects of digital systems and data.
Why do malicious actors want to compromise data and IT systems?
Malicious actors compromise data and IT systems for a variety of reasons, often driven by personal gain, ideological motives, or the desire to cause disruption. Understanding these motivations can help organizations and individuals better defend against cyber threats. Some common reasons why malicious actors engage in cyberattacks include:
- Financial Gain: Many attacks are driven by the desire for financial profit. Malicious actors may steal sensitive information like credit card numbers, bank account details, or personal identification information to commit fraud, identity theft, hold an individual or organization to ransom or sell the stolen data on the dark web.
- Espionage: Nation-states, competitors, or other entities may engage in cyber espionage to steal sensitive government, corporate, or research data for political, economic, or military advantage.
- Disruption and Sabotage: Some attacks aim to disrupt critical infrastructure, services, or operations for political or ideological reasons. These attacks can cause widespread chaos, financial loss, and damage to reputation.
- Ideological Motivations: Hacktivists and groups with ideological or political motivations may compromise systems to raise awareness about certain issues, promote their beliefs, or protest against specific actions or organizations.
- Unintentional Actions: Not all malicious actions are deliberate; some individuals may unknowingly contribute to cyber threats by falling victim to social engineering or being part of a compromised network.
What are the most common types of cybersecurity threats?
There are several common types of cybersecurity attacks that malicious actors use to compromise systems, steal data, and cause disruptions. Here are some of the most prevalent types at the time of writing
- Phishing:
Phishing involves sending deceptive emails or messages that appear to be from legitimate sources in order to trick recipients into revealing sensitive information, such as passwords, credit card numbers, or personal details. Phishing can also lead victims to malicious websites or to download malware.
- Malware:
Malware (malicious software) encompasses a range of malicious programs designed to infect systems, steal data, or cause damage. Types of malware include:
- Ransomware: Encrypts files and demands a ransom for decryption.
- Trojans: Disguised as legitimate software, they give attackers unauthorized access.
- Viruses: Self-replicating programs that attach to files and spread.
- Worms: Self-replicating programs that spread through networks.
- Denial of Service (DoS) and Distributed Denial of Service (DDoS):
DoS attacks overload a target system, rendering it unavailable to users. DDoS attacks involve using a network of compromised devices to flood a target with traffic, making it difficult for the system to function properly or they may stop the system working entirely.
- SQL Injection:
In this attack, attackers manipulate a web application's input fields to inject malicious SQL queries, potentially gaining unauthorized access to databases and sensitive data.
- Cross-Site Scripting (XSS):
Attackers inject malicious scripts into web applications, which are then executed by unsuspecting users' browsers. This can lead to the theft of user data and/or the spreading of malware.
- Social Engineering:
Social engineering exploits human psychology to manipulate individuals into divulging confidential information or performing actions that compromise security.
- Zero-Day (0day) Exploits:
These attacks target vulnerabilities in software or hardware that are not yet known to the vendor or public. Attackers take advantage of these vulnerabilities before patches are developed. Many organizations worry about zero-days as there is no patch for them but they are not as common as the other attacks on this list. When a zero-day is discovered, security researchers will work quickly to make a patch and hence zero-days are generally short lived.

