If you’re into cloud security and Microsoft 365/Entra ID hacking—ethically, of course—you’re going to find this tool invaluable. Meet MAAD-AF (MAAD Attack Framework), a PowerShell-based, interactive tool designed to help you test the security of your cloud environment without unnecessary complexity. With an extensive range of attack modules, it’s built for professionals who want to identify vulnerabilities before attackers do. And let’s be honest, who doesn’t want to be MAAD-AF (mad as f***) about their security? 😤🔥

What is MAAD-AF? 🤯
MAAD-AF is an open-source attack framework specifically designed for Microsoft 365 and Entra ID (Azure AD) security assessments. Instead of manually testing for misconfigurations and weaknesses, MAAD-AF automates the process with 30+ attack modules covering techniques from initial access to data exfiltration.
It also aligns with the MITRE ATT&CK framework, covering around 50% of the cloud-related attack techniques. In short, it’s an efficient way to emulate real-world threats in a safe and controlled manner. Plus, it gives you a valid excuse to go MAAD-AF in your testing. 😉
Why Should You Use It? 🔥
If you manage Microsoft cloud security, MAAD-AF can be a game-changer. Here’s why:
- Simple & Interactive: No complex commands required—just follow the interactive PowerShell workflow.
- Cloud-Specific Testing: Unlike generic attack frameworks, this one is designed specifically for Microsoft 365 & Entra ID.
- Quick Deployment: If you have Windows and PowerShell 5.1, you're ready to go. It literally takes like 1 Minute to get started! 🐳
- Valuable for Red & Blue Teams: Offensive security teams use it to simulate attacks, while defenders use it to strengthen security controls.
- Realistic Threat Emulation: It helps security teams simulate password spraying, token theft, privilege escalation, and persistence techniques within a controlled environment.
- Better Incident Response: Security teams can identify detection gaps and refine their SIEM alerts before an actual attack occurs.
- It’s MAAD-AF, and so should you be: Let’s face it—cybersecurity is frustrating. Might as well embrace it. 😈
How Does MAAD-AF Work? 🕵️♂️
Using MAAD-AF is straightforward. Once installed, you’ll access an interactive PowerShell interface where you can:
- Select attack modules (e.g., token theft, password spraying, privilege escalation).
- Execute them in sequence or test individual techniques.
- Analyze the results and identify security gaps.
Some of the most impactful attack modules include:
- Credential Harvesting: Extract stored credentials, OAuth tokens, and session cookies. Because why should attackers have all the fun? 😏
- Reconnaissance: Identify exposed users, groups, and permissions in your Azure tenant—because knowing is half the battle! 🕵️♀️
- Privilege Escalation: Go from basic user to global admin like you own the place. Just don’t get fired. 🚀
- Persistence Tactics: Simulate backdoors through OAuth app registrations, hidden mailbox rules, or role abuse—aka, the stuff that keeps SOC teams awake at night. 😨
- Exfiltration Methods: Test how an attacker could steal SharePoint files or extract full mailboxes. Who knew hacking emails could be so much fun? (For educational purposes only, of course.) 📬
Who Benefits from MAAD-AF? 🎭
- Red Teams: Want to play the bad guy? MAAD-AF makes it easier to exploit misconfigurations in Microsoft cloud environments—without landing in jail. 🚔
- Blue Teams: Need to up your defense game? Running MAAD-AF helps assess resilience and improve defensive measures—so you don’t have to stress when the real attack comes. 💪
- Purple Teams: Attack, detect, respond, repeat. Rinse and repeat until your security is so tight even you can’t break it. 🔄
Potential Drawbacks ⚠️
Like any powerful tool, MAAD-AF comes with some caveats:
✅ Pro: Open-source and actively supported by the community. $
✅ Pro: Provides extensive coverage of cloud-based attack techniques.
✅ Pro: Helps organizations find weaknesses before attackers do.
❌ Con: Windows-only (no native Linux support at this time—sorry, penguin lovers 🐧).
❌ Con: Running it carelessly could impact production environments—so unless you like awkward meetings with your boss, test responsibly. 🙃
❌ Con: Requires Entra ID & Microsoft 365 permissions for full functionality, so no, you can’t just run this on your coworker’s laptop for fun. 😆
Getting Started with MAAD-AF 🚀
Ready to go MAAD-AF on your security testing? Here’s how to get started:
- Open Powershell 5.1 as Admin 🧑💻
- Clone the Repository:
git clone https://github.com/vectra-ai-research/MAAD-AF- Run It:
cd MAAD-AF
.\MAAD_Attack.ps1- You are going to be greeted by this precious screen 😅
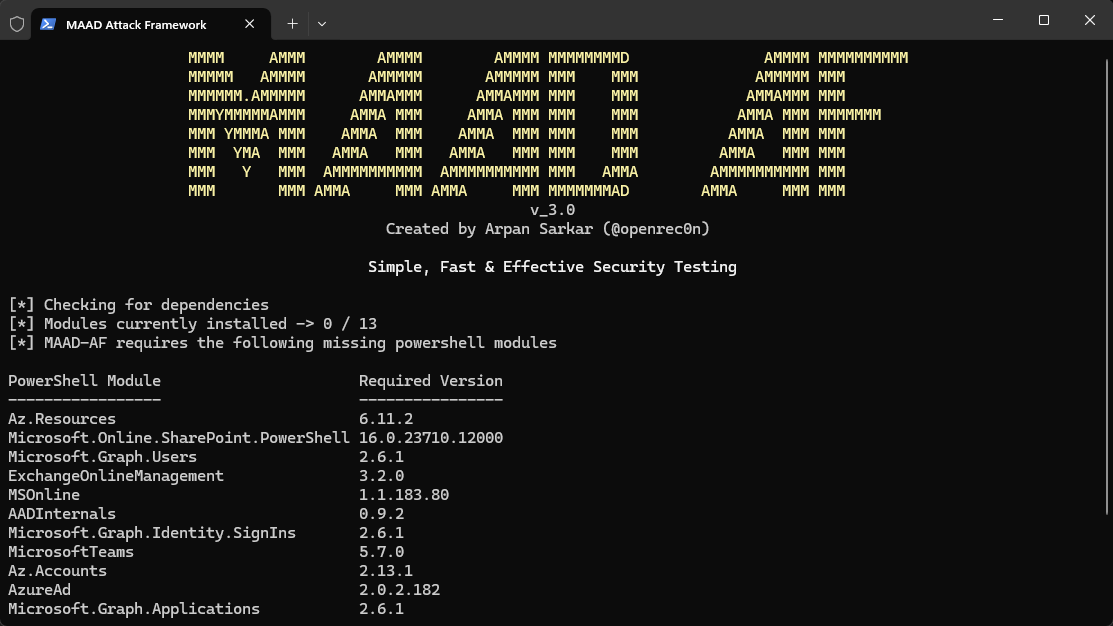
As you can see, we need many PS Modules to get it running - let's install those with a simple "y" 🕶️

Whilst installing all those modules, the AADInternals Module got a little mad and Defender decided to notify me about some shady ass shit - but all good as it says here: https://github.com/Gerenios/AADInternals/issues/98
- Finally - it's Born👶- eh running 📍
We are greeted with this beautiful screen.
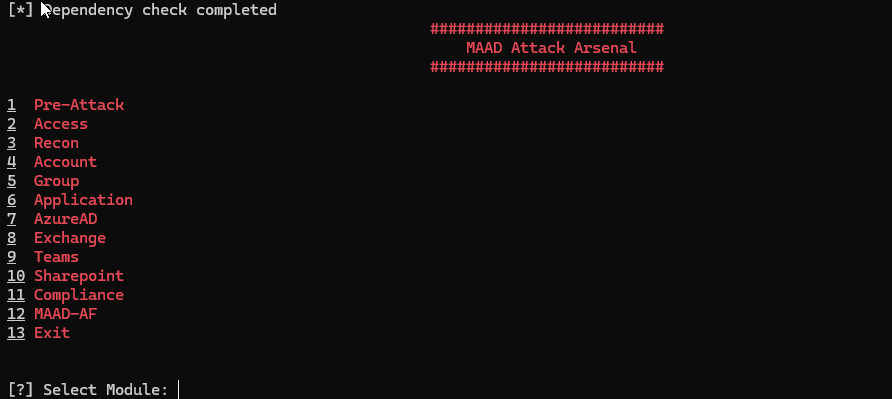
- Pre-Attack
Let's exlore the Pre-Attack Menu 🥪
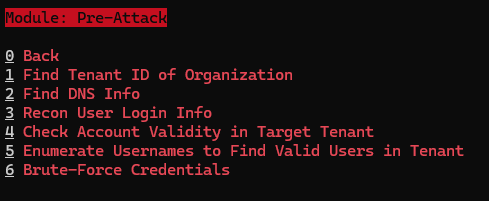
Let's go trough all that ⛳
With technique 1 you can get more info about a Tenant like the Tenant ID.
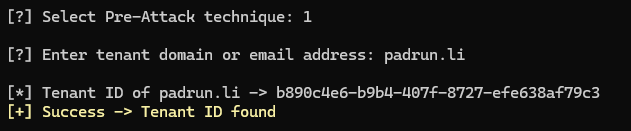
With technique 2 you can get some DNS entries about a Tenant.
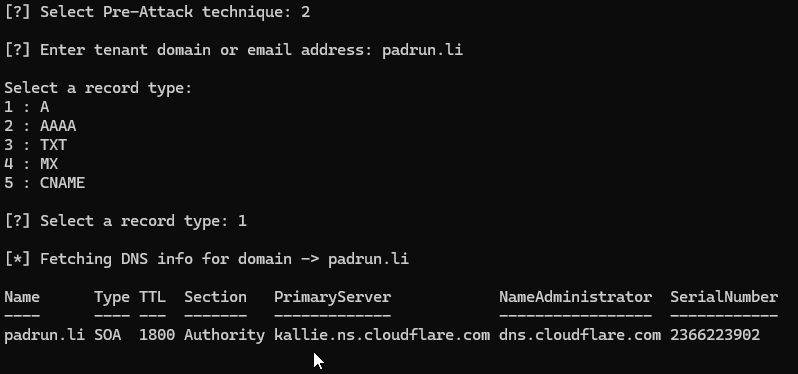
Technique 3 lets you check a User
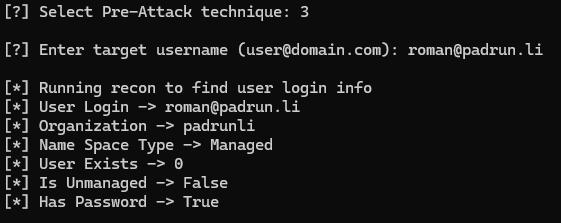
May the technique 4 be with you 🥸 Check if a User exists
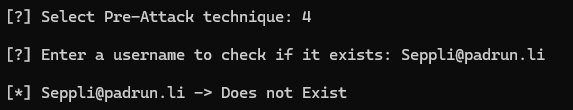
5 and 6 are pretty nice - Enumerate Users and Bruteforce Passwords 🗡️
So create a random Username List and get a Password List and try to breach your Tenant! ╰(*°▽°*)╯
Before using MAAD-AF in a production environment, follow these best practices:
- Use a Test Tenant: Unless you enjoy frantic phone calls from SOC, don’t run MAAD-AF on your live environment without safeguards. ⚠️
- Document Your Findings: Logs, screenshots, and analysis are your friends. Future-you will thank you. 📖
- Fix What You Break: Found a weak spot? Deploy conditional access policies, log monitoring, and endpoint detection rules before someone else exploits it. 🔧
Final Thoughts 🤔
MAAD-AF is an essential tool for Microsoft 365 security testing. Whether you’re identifying attack vectors or strengthening defensive strategies, it offers a structured approach to simulating threats and improving cloud security.
If your job involves securing a Microsoft 365 environment, MAAD-AF should be part of your regular security assessment process. Cyber threats aren’t slowing down—so neither should your testing. 🚦